What Is Onion over VPN and How Does It Work?
Security and privacy are the two main challenges of any modern digitized system. While data is vulnerable during the transfer from one system to another, unauthorized access compromises the privacy of the crucial information.
Hence, the IT world is struggling to develop modern tools and technologies that add an extra layer to the existing security features. The leading security services like Norton offer much-needed protection and the ideal combination of Onion over VPN.

Let us go through the concept of this merging of two different security tools in one, its practical working in safeguarding any system followed by some quick questions on the same. However, before jumping to combination, let us understand Onion and VPN independently.
What is Onion?
The data in the onion network are encrypted and then transmitted through network node series like the onion layers. These network nodes are called the onion routers. The message or data arrives at the destination when the final layer is decrypted.

The protection of the identity is at its best as every next layer knows about the preceding layer details only. It is also called the Tor network.
What is VPN?
The Virtual Private Network or VPN creates a simple private network from any public internet connection.
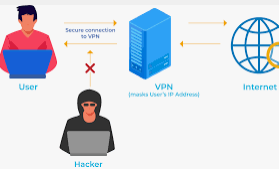
Hence, VPNs mask the IP address of the internet user, and all the actions remain highly untraceable. Therefore, it is perfect for devices at high risk of losing data protection when connected to public internet connections.
What is Onion over VPN?
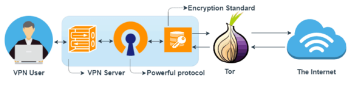
It is common and quite understanding to desire the double benefits of the onion network and VPN. Hence, the Onion over VPN was created. Also known as Tor over VPN, this setup passes the internet traffic through VPN and then through the Onion network before sending it to the internet servers. In other words, the internet user’s identity remains anonymous, and there is no possible option to trace back the connection.

It simultaneously uses the Tor browser and VPN for any inbound or outbound data traffic. The primary purpose of this setup is multi-layer encryption using the benefits of the onion network and VPN at the same time. As a result, it significantly covers the double VPN benefits and offers easy use and high-end security uses.
How does Onion over VPN work?
It is easy to understand the workflow in the Onion over the VPN network. The primary needs of such setup are a good internet connection, VPN, and onion browser. The VPN providers often offer Onion over VPN setup as an in-built feature in their app. Let us understand the inbound and outbound internet data flow separately for the step-by-step working of this effective setup.
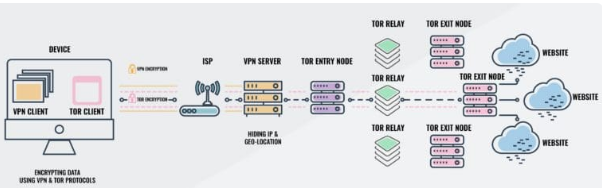
Outbound internet data flow:
- The data from the device is encrypted using the VPN.
- The encrypted data from VPN is again encrypted for adding layer of encryption to the data.
- The double encrypted data is sent to the VPN server.
- Once data is received by VPN, it decrypts the data. The onion browser or Tor browser still encrypts the data from the VPN at this stage.
- According to the requirements, this encrypted data is sent through the Tor browser to the dark web or the clear web.
- For the dark web, data is decrypted once it reaches the destination.
- For clear web, data is decrypted at the node of the onion browser and then is sent to the World Wide Web.
Inbound internet data flow:
- The app, service provider, or website data is sent to the Tor browser.
- The Tor browser receives the data and encrypts it.
- The encrypted data from the Tor network is sent to the VPN server.
- The VPN server adds another layer of encryption to the encrypted data from the Tor network.
- The double encrypted data is sent to the user’s device.
- The tor browser decrypts the data sent to the device.
- The VPN again solves the data from the tor browser.
Why is Onion over VPN used?
Security and privacy may seem like the only two main benefits of Onion over VPN, but there is a lot more technical.
The main advantages of this setup include:
- It offers exceptional levels of seamless internet connectivity as VPN hides the home IP address and prevents it from entering the Onion network. Hence, the system can’t generate the IP address of the user.
- It offers end-to-end data encryption for the user. Even the VPN provider can’t access the data going to the onion network due to the additional encryption layers over the VPN. It is hard to trace back a connection made using this setup. The possibility of an unauthorized node in the onion network is best handled by the VPN that prevents data access to any outside entity.
- It is an easy-to-use setup. Moreover, multiple VPN service providers offer Onion over VPN setup as a built-in feature. Thus, it eliminates the use of any external browser, and this setup is achieved using a single click only.
- It is possible to access the restricted websites that are not possible using the independent onion network. Hence, many users benefit from accessing dark websites with the combination of Onion over VPN.
FAQ:
- What is the simple flow in Onion over VPN?
The internet details from the device go through the VPN server and then pass through the Onion network in this setup. After going through the Onion network, the details reach the World Wide Web.
- What do I need for using Onion over VPN?
The main requirements of using this setup include high-speed internet access, a VPN, and Onion or Tor browser. Depending on the requirements, the user can go for any other browser than the Tor browser.
- How to use Onion over VPN setup?
It is easy to use this security setup. First, the user can open the VPN app with in-built support to this combination. Then, once a VPN connection is achieved, the Tor or Onion browser can be accessed for quick internet surfing.
- Do VPNs offer in-built Onion over VPN support?
Some VPNs like NordVPN, ProtonVPN, etc. comes with in-built support to the Onion over VPN combination. It allows quick access to any application without configuring it to the independent Onion browser.
- Is Onion over VPN different from VPN over Onion?
Yes, both these security settings are quite different from one another. It isn’t easy to set up a VPN over Onion and has a different set of advantages and purposes than the useful combination of the Onion over VPN.
Wrapping Up:
Onion over VPN wins by large numbers when it offers modern security and privacy standards to any device. The protection of browsing history from the independent VPN, hiding real IP address, and performing all critical tasks safely is turning many VPN providers to offer in-built support to this combination.
When compared with the VPN over Onion, the Onion over VPN is easy to setup, understand, and comes with a long list of security and privacy benefits for any personal or professional user.
Popular Post
Recent Post
How to Troubleshoot Xbox Game Bar Windows 10: 8 Solutions
Learn how to troubleshoot and fix issues with the Xbox Game Bar not working on Windows 10. This comprehensive guide provides 8 proven solutions to resolve common problems.
How To Record A Game Clip On Your PC With Game Bar Site
Learn how to easily record smooth, high-quality game clips on Windows 11 using the built-in Xbox Game Bar. This comprehensive guide covers enabling, and recording Game Bar on PC.
Top 10 Bass Booster & Equalizer for Android in 2024
Overview If you want to enjoy high-fidelity music play with bass booster and music equalizer, then you should try best Android equalizer & bass booster apps. While a lot of these apps are available online, here we have tested and reviewed 5 best apps you should use. It will help you improve music, audio, and […]
10 Best Video Player for Windows 11/10/8/7 (Free & Paid) in 2024
The advanced video players for Windows are designed to support high quality videos while option to stream content on various sites. These powerful tools support most file formats with support to audio and video files. In this article, we have tested & reviewed some of the best videos player for Windows. 10 Best Videos Player […]
11 Best Call Recording Apps for Android in 2024
Whether you want to record an important business meeting or interview call, you can easily do that using a call recording app. Android users have multiple great options too. Due to Android’s better connectivity with third-party resources, it is easy to record and manage call recordings on an Android device. However it is always good […]
10 Best iPhone and iPad Cleaner Apps of 2024
Agree or not, our iPhones and iPads have seamlessly integrated into our lives as essential companions, safeguarding our precious memories, sensitive information, and crucial apps. However, with constant use, these devices can accumulate a substantial amount of clutter, leading to sluggish performance, dwindling storage space, and frustration. Fortunately, the app ecosystem has responded with a […]
10 Free Best Barcode Scanner for Android in 2024
In our digital world, scanning barcodes and QR codes has become second nature. Whether you’re tracking packages, accessing information, or making payments, these little codes have made our lives incredibly convenient. But with so many barcode scanner apps out there for Android, choosing the right one can be overwhelming. That’s where this guide comes in! […]
11 Best Duplicate Contacts Remover Apps for iPhone in 2024
Your search for the best duplicate contacts remover apps for iPhone ends here. Let’s review some advanced free and premium apps you should try in 2024.
How To Unsubscribe From Emails On Gmail In Bulk – Mass Unsubscribe Gmail
Need to clean up your cluttered Gmail inbox? This guide covers how to mass unsubscribe from emails in Gmail using simple built-in tools. Learn the best practices today!
7 Best Free Methods to Recover Data in Windows
Lost your data on Windows PC? Here are the 5 best methods to recover your data on a Windows Computer.