What Is Onion over VPN and How Does It Work?
Security and privacy are the two main challenges of any modern digitized system. While data is vulnerable during the transfer from one system to another, unauthorized access compromises the privacy of the crucial information.
Hence, the IT world is struggling to develop modern tools and technologies that add an extra layer to the existing security features. The leading security services like Norton offer much-needed protection and the ideal combination of Onion over VPN.

Let us go through the concept of this merging of two different security tools in one, its practical work in safeguarding any system followed by some quick questions on the same. However, before jumping to combination, let us understand Onion and VPN independently.
What is Onion?
The data in the onion network are encrypted and then transmitted through network node series like the onion layers. These network nodes are called the onion routers. The message or data arrives at the destination when the final layer is decrypted.

The protection of the identity is at its best as every next layer knows about the preceding layer details only. It is also called the Tor network.
What is VPN?
The Virtual Private Network or VPN creates a simple private network from any public internet connection.
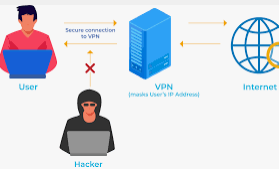
Hence, VPNs mask the IP address of the internet user, and all the actions remain highly untraceable. Therefore, it is perfect for devices at high risk of losing data protection when connected to public internet connections.
What is Onion over VPN?
It is common and quite understandable to desire the double benefits of the onion network and VPN. Hence, the Onion over VPN was created. Also known as Tor over VPN, this setup passes the internet traffic through VPN and then through the Onion network before sending it to the internet servers. In other words, the internet user’s identity remains anonymous, and there is no possible option to trace back the connection.

It simultaneously uses the Tor browser and VPN for any inbound or outbound data traffic. The primary purpose of this setup is multi-layer encryption using the benefits of the onion network and VPN at the same time. As a result, it significantly covers the double VPN benefits and offers easy use and high-end security uses.
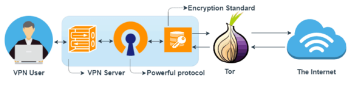
How does Onion over VPN work?
It is easy to understand the workflow in the Onion over the VPN network. The primary needs of such a setup are a good internet connection, VPN, and Onion browser. The VPN providers often offer Onion over VPN setup as an in-built feature in their app. Let us understand the inbound and outbound internet data flow separately for the step-by-step working of this effective setup.
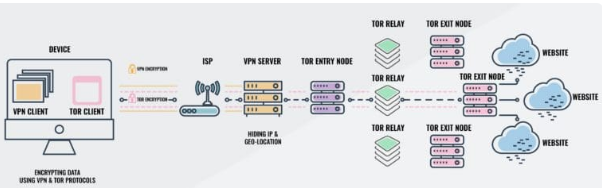
Outbound internet data flow:
- The data from the device is encrypted using the VPN.
- The encrypted data from the VPN is again encrypted for adding a layer of encryption to the data.
- The double-encrypted data is sent to the VPN server.
- Once data is received by VPN, it decrypts the data. The Onion Browser or Tor browser still encrypts the data from the VPN at this stage.
- According to the requirements, this encrypted data is sent through the Tor browser to the dark web or the clear web.
- For the dark web, data is decrypted once it reaches the destination.
- For clear web, data is decrypted at the node of the onion browser and then is sent to the World Wide Web.
Inbound Internet data flow:
- The app, service provider, or website data is sent to the Tor browser.
- The Tor browser receives the data and encrypts it.
- The encrypted data from the Tor network is sent to the VPN server.
- The VPN server adds another layer of encryption to the encrypted data from the Tor network.
- The double-encrypted data is sent to the user’s device.
- The tor browser decrypts the data sent to the device.
- The VPN again solves the data from the Tor browser.
Why is Onion over VPN used?
Security and privacy may seem like the only two main benefits of Onion over VPN, but there is a lot more technical.
The main advantages of this setup include:
- It offers exceptional levels of seamless internet connectivity as the VPN hides the home IP address and prevents it from entering the Onion network. Hence, the system can’t generate the IP address of the user.
- It offers end-to-end data encryption for the user. Even the VPN provider can’t access the data going to the onion network due to the additional encryption layers over the VPN. It is hard to trace back a connection made using this setup. The possibility of an unauthorized node in the Onion network is best handled by the VPN which prevents data access to any outside entity.
- It is an easy-to-use setup. Moreover, multiple VPN service providers offer Onion over VPN setup as a built-in feature. Thus, it eliminates the use of any external browser, and this setup is achieved using a single click only.
- It is possible to access the restricted websites that are not possible using the independent onion network. Hence, many users benefit from accessing dark websites with the combination of Onion over VPN.
FAQ:
- What is the simple flow in Onion over VPN?
The internet details from the device go through the VPN server and then pass through the Onion network in this setup. After going through the Onion network, the details reach the World Wide Web.
- What do I need to use Onion over VPN?
The main requirements of using this setup include high-speed internet access, a VPN, and Onion or Tor browser. Depending on the requirements, the user can go for any other browser than the Tor browser.
- How to use Onion over VPN setup?
It is easy to use this security setup. First, the user can open the VPN app with in-built support to this combination. Then, once a VPN connection is achieved, the Tor or Onion browser can be accessed for quick internet surfing.
- Do VPNs offer in-built Onion over VPN support?
Some VPNs like NordVPN, ProtonVPN, etc. comes with in-built support to the Onion over VPN combination. It allows quick access to any application without configuring it to the independent Onion browser.
- Is Onion over VPN different from VPN over Onion?
Yes, both these security settings are quite different from one another. It isn’t easy to set up a VPN over Onion and has a different set of advantages and purposes than the useful combination of Onion over VPN.
Wrapping Up:
Onion over VPN wins by large numbers when it offers modern security and privacy standards to any device. The protection of browsing history from the independent VPN, hiding real IP addresses, and performing all critical tasks safely is turning many VPN providers to offer in-built support to this combination.
When compared with the VPN over Onion, the Onion over VPN is easy to setup, understand, and comes with a long list of security and privacy benefits for any personal or professional user.
Popular Post
Recent Post
How to Upgrade Computer RAM: Complete Guide
Upgrading RAM is one of the simplest ways to improve a computer. It helps the system feel faster and smoother. Apps open quicker. Browsers handle more tabs. Games and tools run with less delay. Many users search for how to upgrade computer RAM because it gives real results without high cost. You do not need […]
How To Clean Your Computer Keyboard: Complete Guide
A computer keyboard is touched more than almost any other device you own. It is used during work, study, gaming, and casual browsing. Fingers carry natural oils, sweat, and dirt. Small food crumbs fall between keys without notice. Dust settles each day slowly. Over time, this creates a hidden layer of grime. Many users do […]
Computer Mouse Buying Guide for Beginners and Advanced Users
Buying a mouse looks easy at first. Many people think all mouse work the same way. Well, that idea often leads to regret later. A mouse affects comfort, speed, and daily work. It matters for office tasks, gaming, design, and study. The right choice reduces strain and improves control. The wrong one feels annoying every […]
How To Overclock a Computer: A Complete Guide
Overclocking is the process of making your computer run faster than its factory settings. It mainly affects the processor, graphics card, and sometimes memory. Many people choose this method to improve performance without buying new hardware. It is popular among gamers, video editors, and users who run heavy software. When done properly, overclocking can give […]
How To Find Password Saved on This Computer: Complete Guide
Many people forget their login details at some point. It happens often. We create many accounts every year. Each one needs a username and a password. Over time, it becomes hard to remember all of them. That is why computers offer ways to store login details. These saved details help users sign in faster. They […]
How To Open/Access Computer Management & Advanced Tips
Every Windows computer has many hidden tools. Most users never see them. They only use basic settings. They change wallpapers. They install apps. They adjust sound and display. That is enough for daily work. But problems still happen. The system slows down. Storage fills up. Errors appear without warning. At this stage, normal settings do […]
How To Transfer Photos From Android Phone To PC/Laptop [2026]
Moving photos from a phone to a computer is something most people need to do often. Phones fill up fast. Photos also matter more than apps. You may want a safe backup. You may want to edit images on a bigger screen. This guide explains how to transfer photos from Android to PC without stress. […]
Top 9 Browsers With Built-In VPN – VPN Browser
Online browsing is no longer private by default. Every website collects data in some form. This includes location details, device information, and browsing habits. Over time, this data builds a clear picture of user behavior. Many people are now uncomfortable with this level of tracking. A VPN browser helps reduce this exposure. It adds a […]
AI In Cyber Security: Who is Winning, Hackers or Security Companies
Cybersecurity once followed clear rules. Companies built firewalls. Users created passwords. Antivirus tools scanned files and removed known threats. When an attack happened, security teams studied it and added new rules. This method worked for many years. It created a sense of control and stability. That sense is gone today. Artificial intelligence has changed how […]
The Biggest AI-Run Cyber Attacks Of All Time
Artificial intelligence is now part of everyday technology. It helps people search faster. It improves medical research. It supports businesses in making better choices. But AI is not used only for good purposes. Cyber criminals have also learned how to use it. This has changed the nature of cyber attacks across the world. In the […]