Understanding Cyberattack- Top Useful Cyber Security Hacks to Try
Introduction
Most businesses at this time have gone the digital route, opening personalized websites, accessing social media platforms, and more. One can use diverse software like Avast SecureLine VPN to protect their browsing experience. However, the possibility of experiencing cyberattacks is high for most users.
These include various current cyber security issues from external sources like malware attacks, phishing attempts, and hacking. Statistically, crime complaints related to online attacks have increased at a 7% rate and higher around 2020-2021. Depending on the type of issue, one can take steps to protect against cyberattacks. Here, we discuss just that!
Cyberattacks- What Does it Constitute?
Cyberattacks are issues that affect frameworks and computer systems, damaging their regular function. It is one of the current cyber security issues that can steal, disable, or change the information/data of users. Cyberattacks usually target a wide variety of digital platforms and connections consumers use, like PCs, smartphones, internal corporate networks, company computers, etc.
Here are the most common types of cyberattacks that people notice.
- Phishing scams– Malware enters users’ systems through a corrupted link on websites or emails.
- Malware attacks– Different types of malicious software cause defects in devices, like viruses, ransomware, and spyware.
- Service denial attacks– These involve a high amount of traffic flooding that blocks servers, websites, and network systems from normal functioning.
- Spear phishing– Advanced-level phishing attacks like these target executive-level operators in organizations and companies.
- SQL injections– These are harmful programming codes in sites that allow network database access.
- Password attacks– Hackers try to enter accounts and bypass password protection by guesswork.
These types of current cyber security issues can harm the computer system performance, intending to steal data. Cybercriminals get access to internal information, confidential data, and more. Plus, it can harm national security available.
Best Hacks for Cyber Security that One Should Use
One can take multiple steps to improve the cybersecurity of their system, digital devices, or networks. We checked out many of the proclaimed solutions ourselves to finalize the perfect hack in different fields of cyber security. Here, you will learn about the best solutions for the problems, with a detailed breakdown of the sequences.
Solution 1: Use a Password Protection Software
One of the common attacks in terms of cyber security is stealing the password of users. Most digital users use a generic or easily recognizable terminology as their password. These are comparatively easier to guess, and that reduces the strength of the protection for user profiles on different apps.
You can use a strong password manager tool like 1Password to handle different types of passwords in one unified space. So, families with many members or groups in companies can store all passwords in one secure location. You can store different types of information and personal credentials like login details, credit cards, etc. So, it is the best app you can consider for password storage and monitoring.
This app is accessible across different operating system types for desktop (Mac/Windows/etc.), mobile devices (iOS/Android), and browsers (Safari, Chrome, Firefox, etc.).
Features:
- Users can prepare and store an unlimited number of passwords.
- Unlimited access to shared vaults is available.
- Users get admin control to manage and view diverse permissions.
- It is possible to create custom groups for efficient groups.
- 2FA protection for passwords to assure optimized online protection.
- Duo integration benefits are available.
Solution 2: Update the Software
Companies leverage different applications and tools to carry out the system functions to the best limit. The developers of third-party apps do release new updates of the applications often, including advanced new features, optimized interfaces, and strong security fixes.
If you keep the software outdated, it will likely notice multiple errors, slow performance, and become more susceptible to cyberattacks. So, you need to update the apps consistently to improve their safety conditions. Besides that, if you own a device that cannot support the most recent upgrades or future ones, you should opt for alternates.
Solution 3: Monitor the Privileged Users
It is important to monitor all privileged users from an organization’s cybersecurity standpoint. In many cases, the issues that affect different fields of cyber security have an internal source from the team. Users can share the data and carry out cyberattacks, so it is important to use security software that utilizes user activity monitoring to detect suspicious online behavior.
Here, it is recommended to keep relevant information about the monitoring process, data collection metrics, etc., secure and documented. Therefore, it is easier to access the documents at a later time.
Solution 4: Secure the internal workplace network
In companies and for solo entrepreneurs, WiFi networks are useful to operate regularly for online activities. It is useful for fast and secure online browsing work. However, while using WiFi, it is easy for cybercriminals to breach different fields of cyber security.
You should use a stable VPN service like Avast SecureLine VPN. This app makes it easier to access public networks easily without attacks or data loss. You can expect a great speed of online usage and hide your online identity.
Solution 5: Prepare documents and then distribute the cybersecurity policies
Specific companies try out different policies for cybersecurity, many of which are mentioned here. It would be best if you prepared a strategy suitable for your company to use for online security. Create the document for the process to use in future projects.
Additionally, it would help if you informed the employees about the new policies and practices you introduced. Provide the policy-based documents to all employees and/or conduct small group-based training processes.
Solution 6: Update the Security features on your operating system
Sometimes, the main reason why cyberattacks are possible on systems is due to the outdated nature of the OS. You should follow the right steps to update the OS functions on your device. The steps can be different for specific types of device models/versions.
How to do this (Windows)?
Step 1: Go to the Start menu and click on it in the Taskbar. Add “Settings” in the search field and press Enter.
On the other hand, you can click Win + I keys to open the Settings menu instantly.
Step 2: Scroll down the left pane on the menu and click on the “Privacy & Security” option.
Step 3: Open Windows Security.
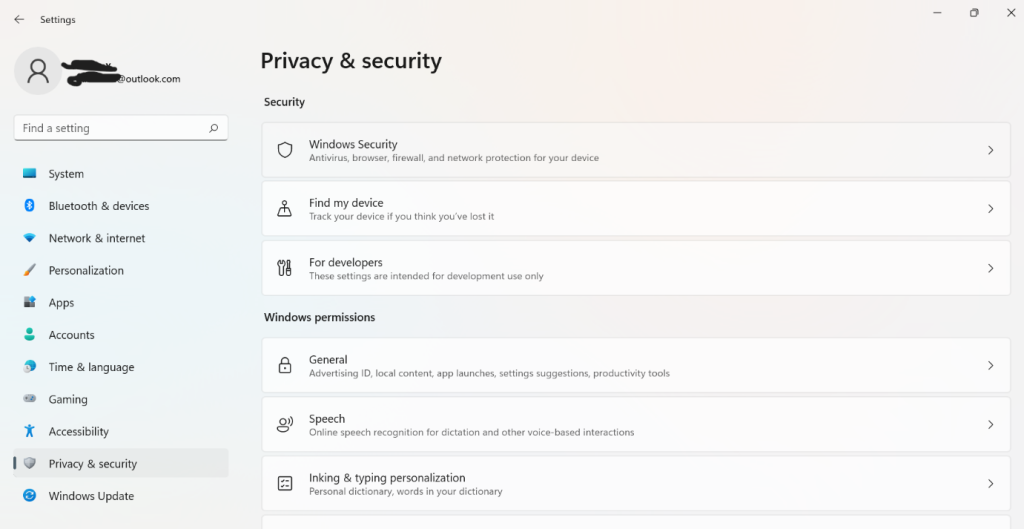
Step 4: Next, choose your security setting option like “Virus & Threat Protection” from the list.
Step 5: Under this window, click on the Quick Scan button.
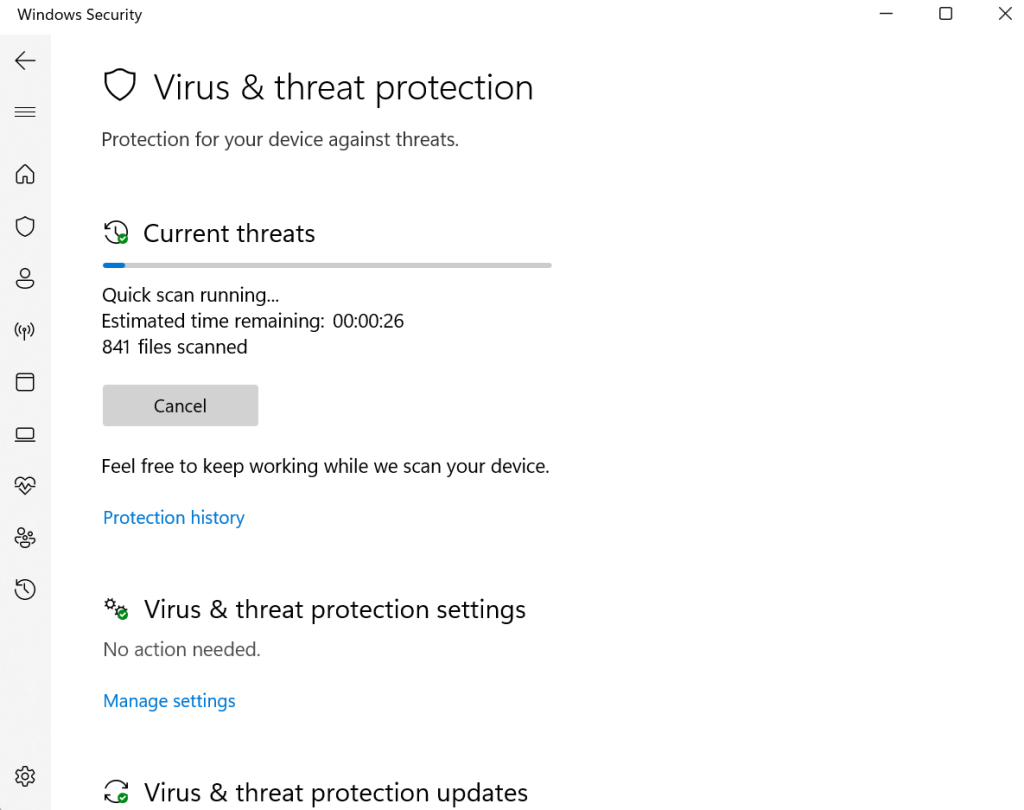
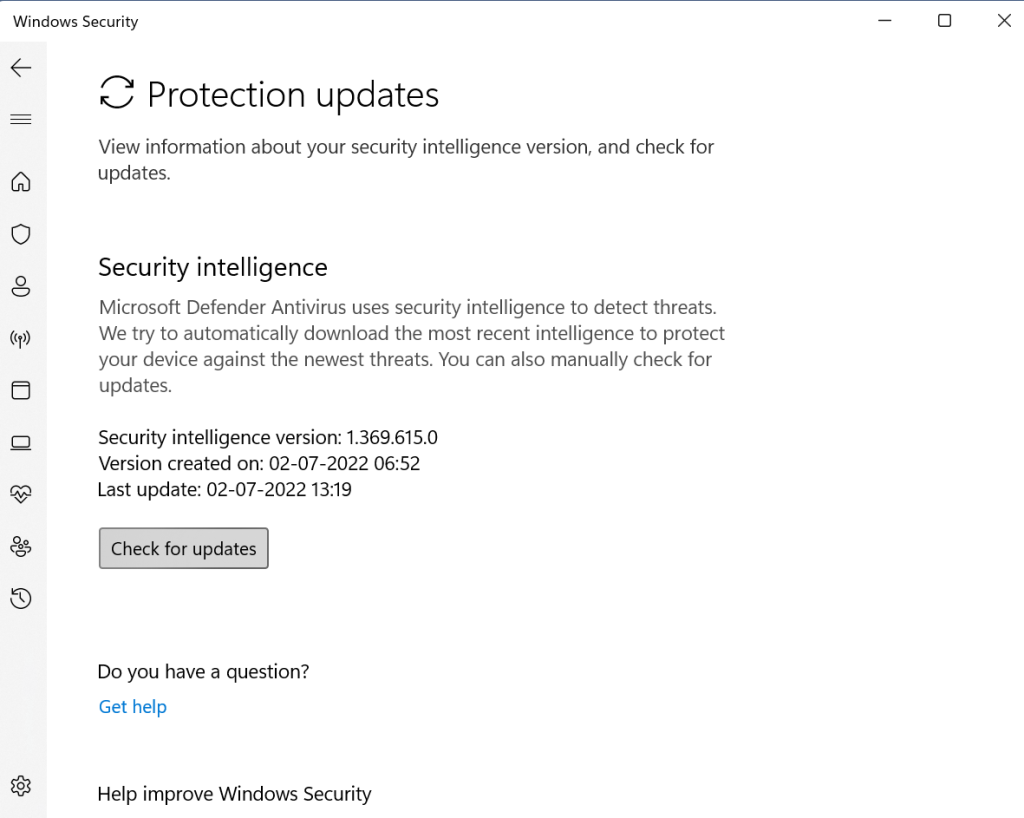
Step 6: Click on Protection Updates > Check for Updates > Run.
Solution 7: Install and use an antivirus software
Viruses, ransomware, spyware, and such issues are some common issues affecting cybersecurity conditions. A top-notch antivirus software contains the right solutions for removing these harmful elements from devices. You can use an option like Avast Antivirus to protect your device and connections fully, browse privately, and reduce performance-based errors.
Solution 8: Use a spam filter
One of the common online cyberattacks is using emails to send malware to devices. To remove these fraudulent emails from your system, you should use a spam filter to check the emails. This spam filter software can detect unwanted and potentially harmful emails using pre-coded configurations. Then, it would remove these defective emails and reduce potential cyber threats.
Solution 9: Back the Data
Data loss is one of the most common results of attacks in different fields of cyber security. Companies often notice a loss of their information, which can cause major difficulties and losses.
Hence, you should backup all data in suitable platforms, like Cloud or a data backup and recovery software. This works as a precautionary step to protect data from getting stolen during a cyber-based attack.
Why opt for cyber security hacks?
The following are the common reasons to try out the different cyber security hacks and improve online safety in companies.
- Regain the lost trust of customers– Clients of companies with low-standard cybersecurity would lose trust that they can protect their data.
- Unavoidable consequences– If the cybersecurity efforts are not up-to-date, law enforcement divisions can charge the brand with negligence.
- Damage control– Companies use strategies to deal with current cyber security issues and breaches to avoid any negative consequences later.
- To reduce heightened cybercrime potential– While advancements in technology do allow the expansion of cybersecurity measures, it also allows cybercriminals to learn new ways to attack cyber defenses.
Conclusion
All in all, these solutions should help you manage the cyberattacks appropriately and optimize your digital safety/privacy. Protect your passwords with a robust password manager, generate unique passwords, operate cyber protection software, and more. Choose the solutions to use based on the main issues you are dealing with, and use them following the right steps.
Popular Post
Recent Post
How to Troubleshoot Xbox Game Bar Windows 10: 8 Solutions
Learn how to troubleshoot and fix issues with the Xbox Game Bar not working on Windows 10. This comprehensive guide provides 8 proven solutions to resolve common problems.
How To Record A Game Clip On Your PC With Game Bar Site
Learn how to easily record smooth, high-quality game clips on Windows 11 using the built-in Xbox Game Bar. This comprehensive guide covers enabling, and recording Game Bar on PC.
Top 10 Bass Booster & Equalizer for Android in 2024
Overview If you want to enjoy high-fidelity music play with bass booster and music equalizer, then you should try best Android equalizer & bass booster apps. While a lot of these apps are available online, here we have tested and reviewed 5 best apps you should use. It will help you improve music, audio, and […]
10 Best Video Player for Windows 11/10/8/7 (Free & Paid) in 2024
The advanced video players for Windows are designed to support high quality videos while option to stream content on various sites. These powerful tools support most file formats with support to audio and video files. In this article, we have tested & reviewed some of the best videos player for Windows. 10 Best Videos Player […]
11 Best Call Recording Apps for Android in 2024
Whether you want to record an important business meeting or interview call, you can easily do that using a call recording app. Android users have multiple great options too. Due to Android’s better connectivity with third-party resources, it is easy to record and manage call recordings on an Android device. However it is always good […]
10 Best iPhone and iPad Cleaner Apps of 2024
Agree or not, our iPhones and iPads have seamlessly integrated into our lives as essential companions, safeguarding our precious memories, sensitive information, and crucial apps. However, with constant use, these devices can accumulate a substantial amount of clutter, leading to sluggish performance, dwindling storage space, and frustration. Fortunately, the app ecosystem has responded with a […]
10 Free Best Barcode Scanner for Android in 2024
In our digital world, scanning barcodes and QR codes has become second nature. Whether you’re tracking packages, accessing information, or making payments, these little codes have made our lives incredibly convenient. But with so many barcode scanner apps out there for Android, choosing the right one can be overwhelming. That’s where this guide comes in! […]
11 Best Duplicate Contacts Remover Apps for iPhone in 2024
Your search for the best duplicate contacts remover apps for iPhone ends here. Let’s review some advanced free and premium apps you should try in 2024.
How To Unsubscribe From Emails On Gmail In Bulk – Mass Unsubscribe Gmail
Need to clean up your cluttered Gmail inbox? This guide covers how to mass unsubscribe from emails in Gmail using simple built-in tools. Learn the best practices today!
7 Best Free Methods to Recover Data in Windows
Lost your data on Windows PC? Here are the 5 best methods to recover your data on a Windows Computer.