What is RAMPAGE Attack?
With each passing day, the number of cyber threats has been increasing exponentially. There are a multitude of viruses, malware, ransomware, malicious apps, and many more to worry about. Hackers have been successfully developing new types of threats.
They have been exploiting any type of weak links in servers, devices, and whatnot. These cyber threats can cause minimal to disastrous damage to you, if your device has been infected. Without appropriate precautionary safety measures, you could be the next victim. Among such dangerous cyber attacks, RAMpage is one. If you want to stay safe from this attack, make sure that educate yourself about it and then secure yourself with proper security measures.
So, What exactly is RAMpage attack?
RAMpage is a row hammer attack that targets the hardware of Android Devices that run on Android 4.0, Ice Cream Sandwich or above. If you’re wondering what exactly a row hammer attack is, it can be defined as an attack that targets the row hammer side effect.
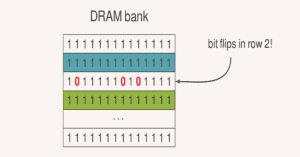
Row hammer is a side effect that is responsible for the memory cells to cause leakage of charges. This side effect is related to the dynamic random access memory. This all started way back in 2012, when Google launched a new element to the Android kernel named ION. It’s responsible for the allocation of memory to different services and apps. RAMpage attacks target these IONs.
These attacks compromise the conditions of these IONs, making them interact with each other electrically, which causes memory flipping between apps and services. Millions of Android devices are potentially vulnerable to this attack.
How does RAMpage attack work?
An application that is equipped with RAMpage targets the ION subsystem and influences a memory bit row and changes the state of that memory row till the bit flipping starts to happen in an adjacent row. Sounds too technical? Well, to be simpler, this malicious threat attacks the ION section of your device and eventually enables the infected app to achieve admin rights to any other app.
For example, this attack can target your device through a normal app and cause information damage. It can exploit sensitive apps like password managers and steal your confidential information. Basically, this attack breaks the isolation between apps and the operating system. It can even take over your device and gain all the administration rights of it.
If you’re not careful about your sensitive data, this attack can steal your information, which is quite dangerous if falls into the wrong hands.
Does it affect your device?
To be precise, every device released post 2012 and runs on Android 4.0 or higher is a target for the RAMpage attack. Basically, these devices use LPDDR2, LPDDR3, and LPDDR4 versions of RAM chips. So, if your device falls under these categories, it is vulnerable to this attack.
But, newer operating systems don’t practice writing the entire information of an application in adjacent cells. So, the information in the memory cells couldn’t be easily exploited. An Android device with a memory of 4GB has 4 billion memory bits. So, exploiting and pinpointing a certain location of information can be almost impossible for the attacker to target.
What should you do?
Google has already identified this attack and started taking security measures against it. As an Android user, you too must follow certain security protocols to ensure that there won’t be any mishaps on your side. The first and foremost step is not to install any suspicious app either from the Play Store or from any external source.
Furthermore, using a security program can enhance the safety of your device, making it hard for hackers to attack your device. Make sure that you use verified apps on your device, exclusively from the Play Store.
Final Verdict
By now, you may have gotten a clear understanding of RAMpage attack. Now, it’s time for you to follow proper precautionary measures to ensure the safety and security of your device and information alike. If you feel that your device has already been attacked, perform a full device scan and report it to Google through their consumer forum.
Popular Post
Recent Post
How to Transfer iPhone Photos to Your Mac (8 Easy Solutions)
Have you clicked a stellar image with your iPhone and now want to upload it on your website or edit it? Then, you can easily transfer your iPhone photos to your Mac to edit them with robust MacOS editing tools and further upload them on the web. Transferring photos from iPhone to Mac can save […]
How to Set Up and Use iCloud on Mac
If you haven’t set up iCloud on your Mac yet, do it now. iCloud is a powerful cloud storage service for Apple users that allow people to back up and synchronize email, photos, contacts, and other files across various devices. iCloud service was introduced in 2011, and it supports MacOS 10.7 or higher. As of […]
How to Create a Guest User Account on Mac
Computers are a very personal thing today. They store all your private documents, photos, videos, and other data. Thus, giving your Mac password to someone else is never a good idea. But what if you have to share your Mac with a colleague or friend for some reason? Sharing Mac’s user password can jeopardize your […]
How to Set Up a New Mac in a Few Minutes
Have you bought or received a brand new Mac computer? Then, you must be on the seventh cloud. Your Mac will open a pandora of several graphics-rich apps and features for you. If you are moving from Windows to Mac for the first time, the change will be really dramatic. At first, all the interfaces […]
How to Clear Browsing History
Are you concerned about what others could see if they use your web browser? Is your browser history clogging up your device and slowing things down? A list of the website pages you have viewed is stored in every web browser. You can remove this listing easily. It will clean your browser history and erase all […]
The Definitive Guide to Managing Your Mac’s Storage Space
Are you struggling with low storage space on Mac? Wondering what is taking up so much space?You are at the right place. Here we will discuss how to reclaim space on Mac. Gone are those days when you used Mac machines only for p rofessional purposes. Now, everything from downloading movies to streaming content, saving […]
Is New World a modern-day RuneScape?
Amazon Game Studios has released an MMO nearly identical to RuneScape, but with a new look, a better PvP system, and a lot more money. Allow me to clarify. New World is influential ‘RuneScape only it’s not RuneScape.’ New World vs. RuneScape 3 New World digs deep into the well of memories and pulls out […]
How To Set Up Voicemail on iPhone 11
Although accessing voicemail is extremely beneficial to you, users should understand how to set up voicemail on their iPhone 11. You can remove, categorize, and play the voicemails from the easy menu. Once you are occupied or unable to pick up the phone, this program will give you info in the style of an audio […]
Best Virtual Machine Software for Windows 10/11 in 2024
A virtual machine software, often known as VM software, is an application that replicates a virtual computer platform. A VM is formed on a computer’s underlying operating platform, and the VM application generates virtual CPUs, disks, memory, network interfaces, and other devices. Virtual machine solutions are becoming more popular because of the flexibility and efficiency […]
How to Be a Better Project Manager
The role of the project manager is to provide you and your team with the goals, organizational systems, and feedback necessary for creating a positive workplace result. Everything from coding to content development can benefit from a high-quality project manager. This article will cover some of the actionable steps you can take to become better […]